CSOI directly addresses the core vulnerabilities of legacy networking which continue to expose critical infrastructure to threat actors, sponsored nation state cyber criminals, and related. Our approach overcomes the vulnerabilities of legacy networking with rigorous cryptographic identity-defined verification, and continuous trust validation.
CSOI achieves a new state of cyber resilience that is effective, simple to deploy and manage, and one based on cryptographic identity-networking. Let’s look at some of the key elements of CSOI, what it provides, and how it elegantly integrates within your network environment.
The Solve of Vulnerable IP-Networking:
Network Environment Agnostic:
CSOl provides seamless integration with any networking topology without need for rip and replace. Stated another way, CSOI has compatibility to run on any network environment with little to no modification.
Cloaking & Segmentation:
CSOI protects critical infrastructure through effective networking segmentation & cloaking, making protected infrastructure invisible to cyber threats, while strengthening the overall cyber defense security posture of an agency or enterprise.
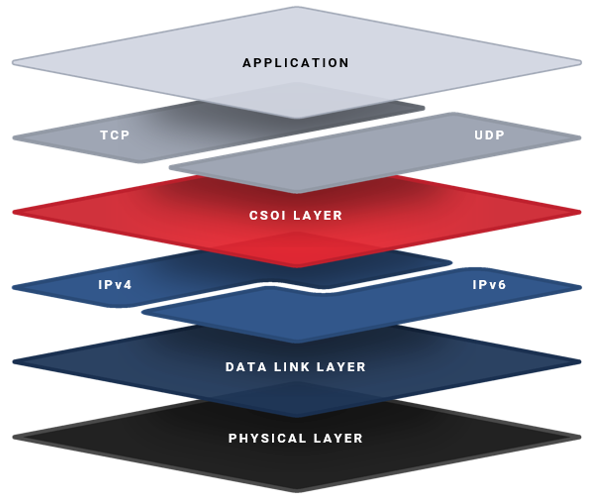
IMPRES CSOI provides an Authentication and Validation SHIM between transport and network layers within the OSI Model
Traditional Network Architecture